
12,000 Ollama Instances Exposed: When 'Local-First' Meets the Real World
Ollama is one of the most popular tools for running large language models locally. 100,000+ stars on GitHub, millions of downloads, the default choice …
Read More
7 min read

Ollama is one of the most popular tools for running large language models locally. 100,000+ stars on GitHub, millions of downloads, the default choice …

Every Selenium Grid instance deployed with Firefox nodes is vulnerable to unauthenticated remote code execution. Not “was” - is. The …

One of our scans recently picked up an open vector database. Inside: over a hundred pages of internal documents related to uranium mining operations. …
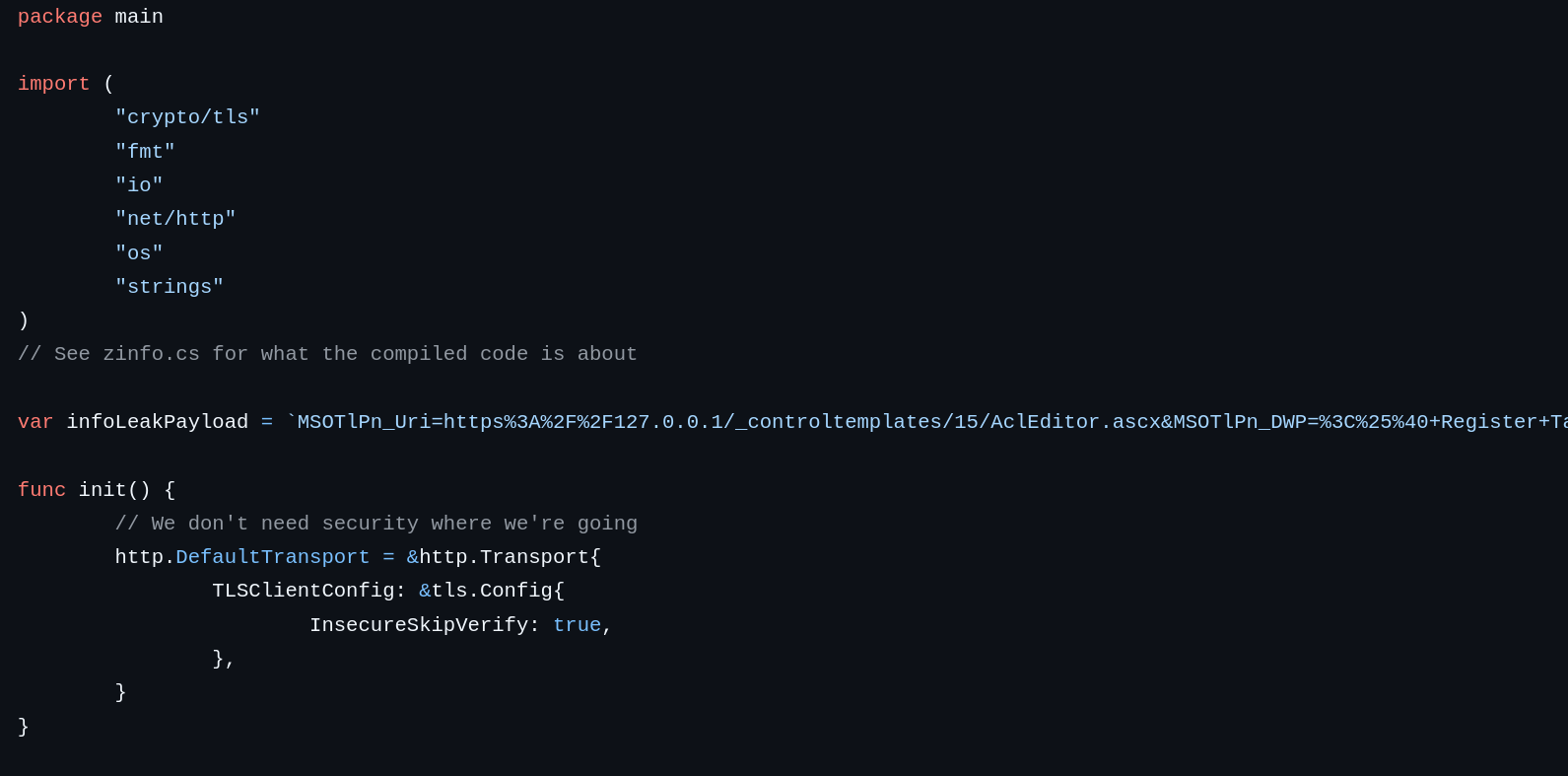
Exploring our adventure while building detection for SharePoint exploitation and vulnerability.